0wn!ng LazySysAdmin: 1
Hi,
In this post I am going to write on how I owned LazySysAdmin: 1 machine which is hosted on Vulnhub.
As usual, I start with an arp-scan and discover the target IP address.
Next, starts the port-scan.
I decided to first enumerate the webpage:
Enumeration reveals that wordpress and phpmyadmin is running.
It is clear that the name of the admin is "togie" which may come to use at a later time.
Next, I searched through the website and there are files with directory listing, etc but I had hit a roadblock on web service.
I decided I shall look over to smb ports 139 and 445.
using smbclient and checked if null sessions are enabled and my guess is correct.
There are some interesting files here.
After further digging I have two information points:
1. in wp-config, we see dbusername and password is present.
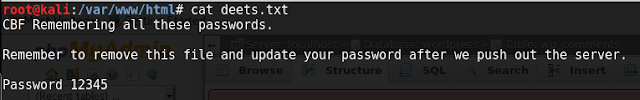
2. File deets.txt has a clue:
Now, with username "Admin" and password "TogieMYSQL12345^^" I can login to phpmysql as phpmysql password is same as mysql password.
Its a lazyAdmin machine so maybe there is a password re-use?
I tried the same password for wp-admin login and could login:
Given the mysql password as "TogieMYSQL12345^^" I tried "TogieSSH12345^^" for ssh service but it failed.
I remember I had the deets.txt I was able to get from smb share.
With username as "togie" and password "12345" I got ssh shell but it is restricted bash.
So I tweaked my ssh login to escape the rbash:
As you can see user "togie" is in sudo group so a sudo -i makes us root user.
Going for the flag:
Conclusion:
This boot2root was good but could have been a little more challenging, specially privilege escalation.
Thanks to the author, Togie Mcdogie who put in the efforts to build the machine and to Vulnhub for hosting it.
-n1ghtcr4wl3r
In this post I am going to write on how I owned LazySysAdmin: 1 machine which is hosted on Vulnhub.
As usual, I start with an arp-scan and discover the target IP address.
Next, starts the port-scan.
I decided to first enumerate the webpage:
Enumeration reveals that wordpress and phpmyadmin is running.
It is clear that the name of the admin is "togie" which may come to use at a later time.
Next, I searched through the website and there are files with directory listing, etc but I had hit a roadblock on web service.
I decided I shall look over to smb ports 139 and 445.
using smbclient and checked if null sessions are enabled and my guess is correct.
There are some interesting files here.
After further digging I have two information points:
1. in wp-config, we see dbusername and password is present.
2. File deets.txt has a clue:
Its a lazyAdmin machine so maybe there is a password re-use?
I tried the same password for wp-admin login and could login:
Given the mysql password as "TogieMYSQL12345^^" I tried "TogieSSH12345^^" for ssh service but it failed.
I remember I had the deets.txt I was able to get from smb share.
With username as "togie" and password "12345" I got ssh shell but it is restricted bash.
So I tweaked my ssh login to escape the rbash:
As you can see user "togie" is in sudo group so a sudo -i makes us root user.
Going for the flag:
Conclusion:
This boot2root was good but could have been a little more challenging, specially privilege escalation.
Thanks to the author, Togie Mcdogie who put in the efforts to build the machine and to Vulnhub for hosting it.
-n1ghtcr4wl3r












Comments
Post a Comment